【速報】クラウドファンディングを行います!ご協力お願いします!

クロックワークメモリオン【完全版】制作・発売に向け、
クラウドファンディングが開始されました!!
■クラウドファンディングって何?
クラウドファンディングとは、アイデアを実現するために必要な創作費用を、 そのアイデアに共感した友達・ファン・ソーシャルのつながり、そして世界中の人々から少額ずつ 集めることができるプラットフォームです。
当クラウドファンディングはCAMPFIREのプラットフォームにて行われます。
【プロジェクトのページ】
https://camp-fire.jp/projects/view/105887
■プロジェクトの概要
当プロジェクトの目的は「お友達に自信を持ってオススメできる“実在するカードゲーム”」を作ることです。
また、現在公開されているバージョンからいくつかのデザイン、ルールなどが一新されます。

※カードは開発中のものです
【変更点】
・カードサイズの変更(大きく)
・テキストのリサイズ(大きく)
・フレイバーテキストの追加
・イラストのリニューアル
・ルールの最適化
・能力の最適化
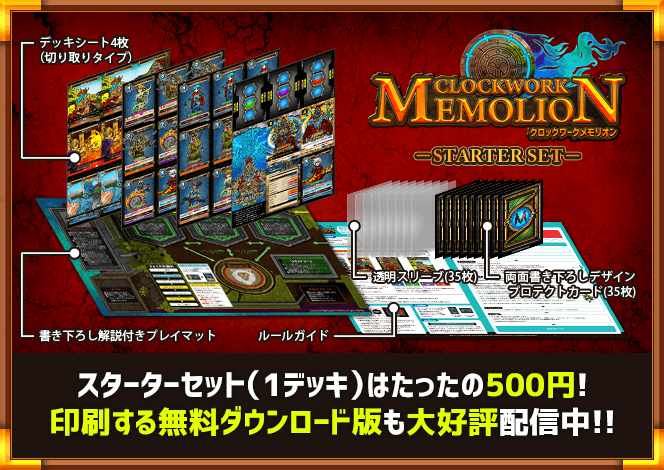
クラウドファンディングでは「クロックワークメモリオン」の基本セットとなる4種類デッキ(カード、プレイガイド、パッケージ等)の制作費(約20万円)を集めることを目的としています。
支援は1,000円から可能で、支援者には特典として発売予定の商品先行入手権(特別価格)や限定カードなどを用意いたします。
<プロジェクト概要>
内容 :カードゲーム「クロックワークメモリオン」の商品化プロジェクト
目標金額:20万円
期間 :2018年11月6日(火)~2018年1月14日(月)23:59:59
▼クラウドファンディング参加方法
下記URLよりページにアクセスいただき、ご希望の支援方法を選んでいただき、お申し込みください。
【プロジェクト】
https://camp-fire.jp/projects/view/105887
■今後の展望
無事目標金額に達成した場合は、2019年3月よりリターン商品を発送致します。
さらに2019年5月25日開催予定の「ゲームマーケット2019春(東京ビッグサイト」に出展し、ティーチング(初心者のためのルール説明)と販売を行います。
その他、サイトをリニューアルしプレイヤーへのフォローや大会情報、ランキング、情報交換の場などを設置致する予定です。
また、目標金額に到達した場合のストレッチゴール(第2、第3のゴール)を設けていますので、支援金がより募れば支援者への特典が追加されていきます。